Solutions
/
Enterprise
Cydarm's Cyber Response Management platform provides a whole-of-business approach to security operations in enterprise environments. Cydarm for Enterprise takes into consideration the needs of large organizations, prioritizing integrations of existing tech stacks, complex business models, reporting, and controlling access to sensitive information across differing levels of trust and location.
Designed to support a constantly changing landscape, Cydarm for Enterprise provides capabilities that cover a comprehensive set of needs for enterprise security operations teams. These include case management, data enrichment, integrations, editable playbooks, reporting, collaboration, and response time SLAs.
Security operations teams now need to analyze, respond, collaborate, communicate, report, and comply. Management and executive leadership teams focused on the people and process aspect of a function need efficient and effective ways to support and enable distributed staff.
Cydarm for Enterprise is utilized in security environments across multiple global organizations and regulated industries, enabling compliance, efficiency, and data-informed decision making for more effective cybersecurity.
Efficient and effective cyber response at scale
Collaborative
Collaborate in real-time across distributed locations with virtual and hybrid staff. Utilize "need-to-know" granular attribute-based access controls on-platform, and report quickly with automatic data redaction based on data type and sensitivity.
Comprehensive
Cydarm for Enterprise provides a holistic, top down approach to enterprise security operations and incident response while preventing data leakage. Integrates with SIEM, Messaging, ITSM, Authentication, and more. On-premise or cloud-hosted.
Consistent
Build cyber resilience by performing consistent investigations with inbuilt and editable playbooks and workflows. House sensitive incident response plans, asset registers, and security response data away from potentially compromised internal systems during a breach.
Coordinate an integrated response
with Cydarm
for Enterprise
Coordinating hybrid and virtual teams across multiple locations and time zones can be challenging. As is the operation of numerous separate platforms as part of standard incident response processes. Cydarm unifies the response efforts into one place, supporting security operations wherever your team is located.
With multiple integrations available, Cydarm for Enterprise supports automated case creation from emails, Splunk, AWS GuardDuty, Azure Sentinel, LogRhythm, and more. Take relevant communications directly to messaging platforms like Slack, Teams, SMS, and PagerDuty. Connect major ITSM platforms like ServiceNow and Jira to create tickets and cases.
Cydarm's granular attribute-based access controls allow the integration of different levels of trust across your organization. Apply access control types limiting visibility from entire cases through to individual comments or data types. Auto-redact sensitive data using access control types when generating reports for internal and external stakeholders.
Define and establish incident response processes
Create and disseminate response playbooks
Assign and prioritise incidents and playbook tasks
Collaborate beyond the security operations centre
Arming the right stakeholders with the right information during a cyber incident is paramount to managing effective, whole-of-organization responses to threats.
This includes communicating to key executives about ongoing incidents, reporting effectively to regulators, and coordinating messaging to customers and the supply chain.
Cydarm’s attribute-based access control model allows any team to bring key stakeholders and other audiences on-platform, giving access to only the relevant data and nothing more.
Playbooks
Cybersecurity teams often rely on documented processes that are stored in multiple locations and remote sites. Unfortunately, this gives them increased potential to become outdated and irrelevant as incidents and threats evolve. Cydarm implements playbooks using a consistent, open-source format to describe incident response workflows which can be shared with communities of interest. Playbooks disseminate the most recent knowledge and methodologies to team members quickly, resulting in improved organizational ability to adapt to new threats.
- Create playbooks whilst mixing and matching playbook tasks
- Assign playbook actions to team members
- Timestamped response actions are recorded upon task completion
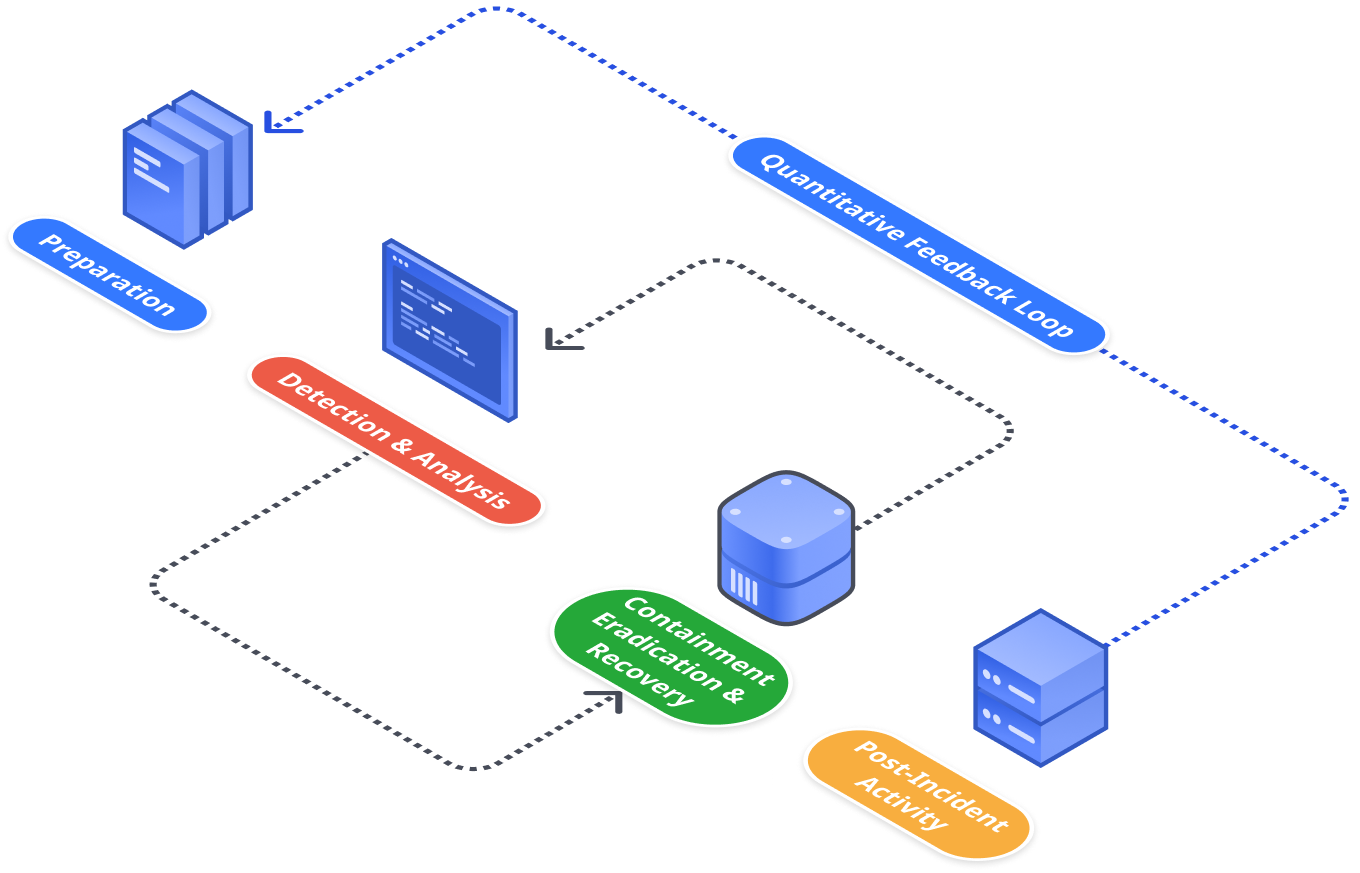
A data-driven approach to security
Getting management support for new budgets to obtain security controls and mitigate perceived security risks is one of the most challenging aspects of being a security professional. Tracking cyber incidents is critical to understanding security control absences or deficiencies in your IT environment. Cydarm tracks incident types occurring so you can easily report on and prioritize your investment on the highest threats to your organization
- Use MITRE ATT&CK to understand threats and incident occurrences
- Report on incident types occurring in your network
- Understand incident trends and changes in the threat environment