Give your critical apps the scrutiny they deserve
With 74% of breaches involving authenticated users, relying solely on unauthenticated testing is not enough.
All applications carry risk when compromised by attackers, but not all risks are equal. While modern Attack Surface Management (ASM) solutions are effective at identifying exposures from unauthorized users, they miss subsurface issues associated with authorized user access. This oversight, combined with the dynamic nature of constantly changing functionality, could put your business-critical apps in peril.
A Proactive Approach to Application Security
Fortify the Security of Your Most Critical Apps
CAPT strengthens the security of business-critical custom applications, with authenticated assessments delivered through a user-friendly portal and expert analysis to uncover high-risk exposures, deliver real-time insights, and provide ongoing threat surveillance for maintained resilience.

Amplify Analysis on Critical Applications
Different applications, different risks. Expand testing on those that matter most.
Covers New and Existing Applications
Allows your security team to submit high-priority applications for assessment, including those in the existing CASM inventory (CASM users only). All applications assessed by CAPT undergo the robust discovery process powered by the Cosmos platform.
Keeps Pace With Your Business
Features a flexible service consumption model that makes it easy and cost-effective to conduct testing when new applications are deployed and functionality changes.
Accelerates Time-to-Testing
Eliminates lengthy scoping procedures by offering a straightforward and secure interface for submitting application’s relevant details, and credentials.
Illuminate the Highest Risks to Your Business
Miss nothing. Verify everything. We zero in on the most dangerous threats.
Maps Every Corner of the Application
Constructs a detailed map of the entire attack surface using an intelligent crawl engine that fingerprints the application’s characteristics with detailed analysis of input/output, DOM state, tech stack fingerprints, and APIs.
Discovers All Potential Threats
Employs advanced fuzzing and vulnerability identification to uncover unauthenticated and authenticated avenues of attack, including access controls, session management, business logic flaws, data handling, encryption, and more.
Verifies Real-World Exploitability
Eliminates the overwhelming noise of automated solutions with expert application testers that safely confirm exploitability and potential business impact under real-world attack conditions.
Scores Severity Based on Verified Threat
Assigns ratings based on the potential to access to sensitive systems and data post-exploitation, so you can address the most critical exposures first.

Quickly Eliminate Attacker Opportunity
Speed is the attacker's advantage. We make it yours.
Extends Security Expertise
Provides live communication and access to testers via a dedicated and encrypted channel to answer inquiries and support further validation.
Delivers Real-Time Insights
Provides a centralized, up-to-date view of what your CAPT team is finding and analyzing. Insights includes findings, impact analysis, remediation guidance and a prioritized list of critical and high severity issues.
Targets Remediation with Actionable Findings
Delivers a focused list of validated exposures, prioritized based on the potential to expose sensitive systems and data, complete with impact analysis and actionable guidance for remediation.
Confirms Applications Are No Longer At Risk
Supplies unlimited on-demand remediation testing to validate that exposures have been fully resolved and are no longer susceptible to compromise.

Stay Resilient in the Face of Change
Threats and applications are constantly evolving. Move forward with confidence.
Stays Ahead of Emerging Threats
Uses a specialized team of experts to proactively scout for rapidly developing threats. When a relevant threat is identified, your application is assessed and validated for vulnerability before attackers have an opportunity to strike.
Monitors for Threat Landscape Shifts
Continuously surveys the threat landscape for new categories of vulnerabilities with periodic rescans and assessment to ensure applications remain fortified.
Supports Continuous Improvement of Your Security Posture
Re-evaluates previous indicators of vulnerability to determine new areas of risk and discover opportunities to improve your application’s resilience.
Reassesses Application Changes
Offers simple to initiate, add-on testing, to identify and validate vulnerabilities in new application features or significant system changes.
Our difference. Your outcomes.
Prioritize and protect the custom applications that are critical to your business with CAPT.
Be confident in the applications that matter most
Get a deeper level of assessment of the applications that are critical to your business with a threat- and impact-driven approach.
Uncover the full spectrum of potential exposures
From initial breach points to deeper vulnerabilities associated with authenticated access, we uncover all application security risks.
Act only on exploitable threats
Our testers rigorously validate exploitability under real-world attack conditions, guaranteeing that every finding necessitates a response.
Prioritize findings against business impact
Our findings connect scoring classifications to activities proven to jeopardize essential systems, data, and services.
Close the window of vulnerability
CAPT provides real-time access to testers, unlimited remediation testing, and actionable guidance to outpace modern threats.
Maintain defensive resilience
Ongoing surveillance for shifts in the threat landscape and revisiting indicators of vulnerability ensure your application's defenses remain ahead of attackers.
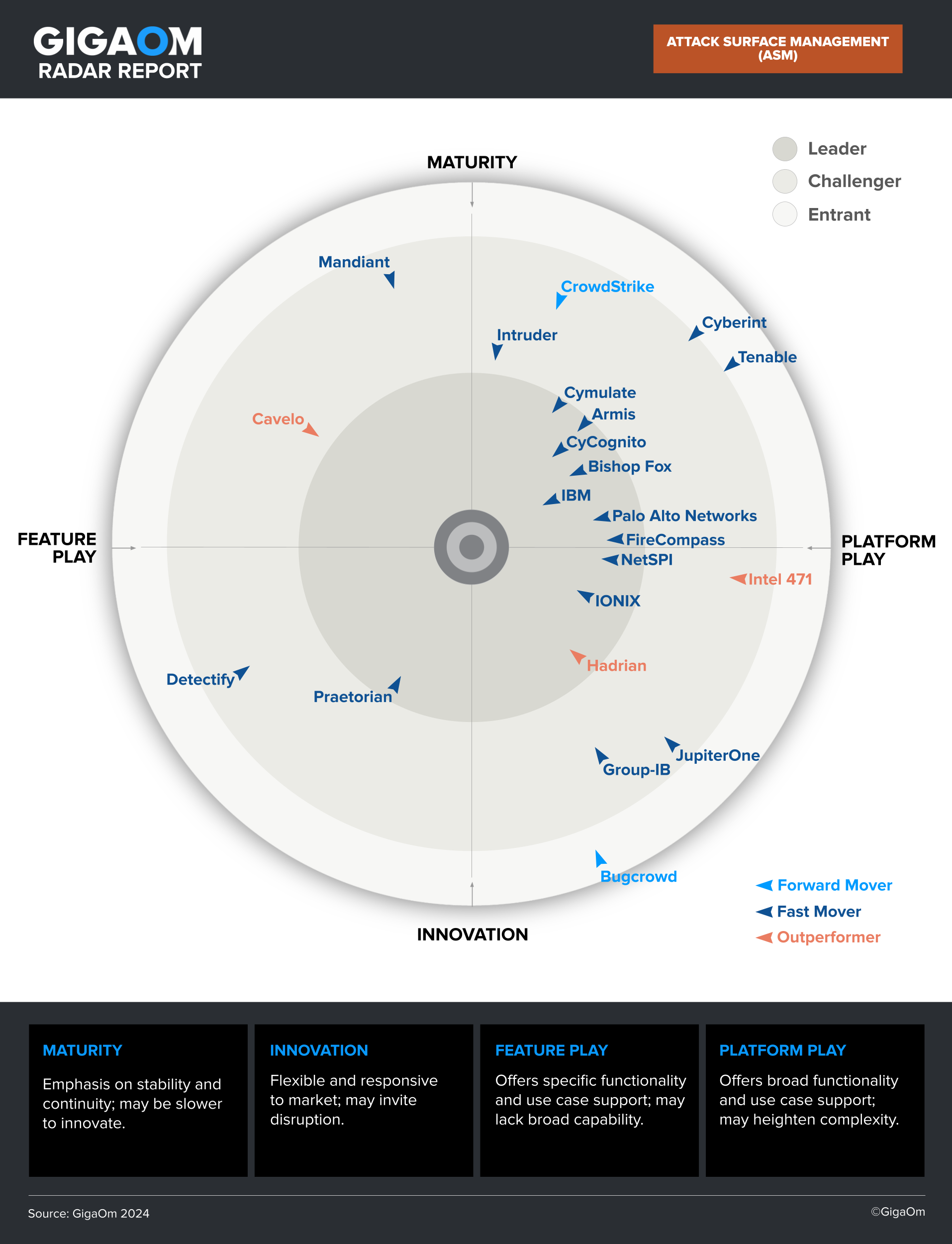
Discover an Award-Winning Difference
Cosmos a "Leader" in GigaOm ASM Radar for 3rd Year in a Row
In its assessment of the top Attack Surface Management providers, GigaOm once again named Bishop Fox a Leader and Fast Mover for its Cosmos solution.
"Bishop Fox’s positioning as a Leader in the Maturity/Platform Play quadrant on the Radar reflects its well-established presence in the market, combined with a comprehensive and reliable platform-based approach to ASM."Cosmos earned scores of "Superior" to "Exceptional" across all Business Criteria evaluated by the analyst firm — including Flexibility, Scalability, Cost, and Ease of Use. Read the report to learn more.
Related Resources
Check out these additional Cosmos resources.

Ponemon Institute Report 2023
In a new study conducted with Bishop Fox, the Ponemon Institute surveyed nearly 700 security and IT practitioners who actively employ offensive security practices. The analysis explores where enterprises are focusing offensive security efforts and the drivers behind them.

Cosmos Datasheet
| Learn how Cosmos combines attack surface management with expert-driven penetration testing to help security teams identify and remediate dangerous exposures before attackers can exploit them. |

Application Security Portfolio Datasheet
| From strategic engagements that integrate security across the software development life cycle, to manual and automated testing, our experts uncover tactical and strategic security issues that real-world adversaries specifically target. |
Are you ready? Start defending forward.
Are you ready to uncover your digital footprint and get a real-time, attacker’s view of your perimeter? Request a demo to see the Cosmos platform in action.