Data communication & computer networking: Huffman algorithm
- 1. Introduction to Data communication Topic : Huffman Algorithm Lecture #12 Dr Rajiv Srivastava Director Sagar Institute of Research & Technology (SIRT) Sagar Group of Institutions, Bhopal http://www.sirtbhopal.ac.in
- 3. • In computer science and information theory, a Huffman code is a particular type of optimal prefix code that is commonly used for lossless data compression. • Huffman coding is a form of statistical coding • Not all characters occur with the same frequency! • Yet all characters are allocated the same amount of space
- 4. Huffman Encoding • Huffman coding, however, makes coding more efficient. In this mechanism we assign shorter codes to characters that occur more frequently and longer codes that occur less frequently. • For example, E and T, the two characters that occur most frequently in the English language, are assigned one bit each. • C,G,K,R,S,U and W are the next most frequently and are assigned three bits each , and so on.
- 5. • In a given piece of text, only some of the characters will require the maximum bit length. • The overall length of the transmission, therefore, is shorter than that resulting from fixed-length encoding. • Difficulty arises, however, if the bit patterns associated with each character are assigned randomly. • Consider the example given figure.
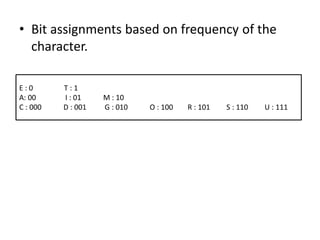
- 6. • Bit assignments based on frequency of the character. E : 0 T : 1 A: 00 I : 01 M : 10 C : 000 D : 001 G : 010 O : 100 R : 101 S : 110 U : 111
- 7. • Multiple interpretations of transmitted data code sent First interpretation Second interpretation Third interpretation 00101010011110 0 01 010 100 1 111 0 E I G O T U E 00 10 101 0 01 110 A M R E I S 001 010 100 111 10 D G O U M
- 8. • Huffman coding is designed to counter this ambiguity while retaining the bit count advantages of a compression code. • Not only does it vary the length of the code based on the frequency of the character represented, but each character code is chosen in such a way that prefix of another code. • For example, no three-bit code has the same pattern as the first three bits of a four or five- bit code.
- 9. Character Tree • Using the character set from the example above, let’s examine how a Huffman code is built. 1. First we organize the entire character set into a row, ordered according to frequency from highest to lowest (or vice Versa). Each character is now a node at the leaf level of a tree. E = 15 T = 12 A = 10 I = 08 M = 07 N = 06 C = 05 D = 05 G = 04 K = 04 O = 03 R = 03 S = 02 U = 02
- 10. 2. Next, we find the two nodes with the smallest combined frequency weighting and join them to form a third node, resulting in a simple two-level tree, the weight of the new node is the combined weight of the original two nodes. This node, one level up from the leaves, is eligible to be combined with other nodes. Remember the same weight of the two nodes chosen must be smaller than the combination of any other possible choices.
- 11. 3. We repeat step 2 until all of the nodes, on every level, are combined into a single tree.
- 14. Assigning the codes • Once the tree is complete, we use it to assign codes to each character. First we assign a bit value to each branch (see figure F.7). Starting from the root (top node). • We assign 0 to the branch and 1 to the right branch and repeat this pattern at each node. • Which branch becomes 0 and which becomes 1 is left to the designer as long as the assignments are consistent throughout the tree.
- 16. • Code assignment table. Character Frequency Code Character Frequency code E 15 100 D 5 0101 T 12 111 G 4 0110 A 10 000 K 4 0111 I 8 001 O 3 11000 M 7 1010 R 3 11001 N 6 1011 S 2 11010 c 5 0100 U 2 11011
- 17. DECODING • A message encoded in this fashion can be interpreted without ambiguity, using the following process : 1. The receiver stores the first three bits received in memory and attempts to match them with one of the three bit codes. If a match is found, that character is selected and the three bits are discarded. The receiver then repeats this step with the next three bits.
- 18. 2. If a match is not found, the receiver reads the neat bit from the stream and adds it to the first three. It then attempts to find a match among the four-bit codes. If a match is found, the corresponding character is selected and the bits are discarded. 3. If a match is not found, the receiver reads the neat bit from the stream and tries to match all the five bits to one of the five bit codes. If a match is found, the character is selected and the bits are discarded.
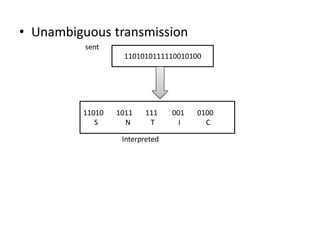
- 19. • Unambiguous transmission sent Interpreted 1101010111110010100 11010 1011 111 001 0100 S N T I C
- 20. Thank You Dr Rajiv Srivastava Director Sagar Institute of Research & Technology (SIRT) Sagar Group of Institutions, Bhopal http://www.sirtbhopal.ac.in