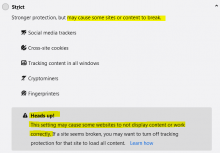
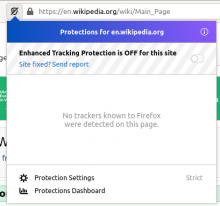
[Update] As of Feb 2021, this is now reportedly a problem in Firefox, and will be soon in Chrome.
[Older notes]
As noted at Meta:Babel CentralAuth login state does not seem to propagate across domains in Safari.
Steps to reproduce:
- Open Safari
- go to https://en.wikipedia.org/
- click 'Login'
- check 'Keep me logged in'
- enter username/password and click the button
- see that you are logged in on enwiki
- go to https://de.wikipedia.org, confirm logged in on dewiki
- go to https://commons.wikimedia.org, notice not logged in on commons
- go back to https://en.wikipedia.org, confirm still logged in on enwiki
Tested Safari 12.1.1 (14607.2.6.1.1) on macOS 10.14.5. Firefox 67.0.4 on the same machine using the same account retains login across domains just fine.
Is there maybe a cookie issue with Safari's anti-tracking/anti-cookie stuff? Or something that might strike randomly and only happens to be hitting Safari when we're testing it? Is this a known issue I should merge the report with?
SSO, cross domain, requestStorageAccess, hasStorageAccess